So I use Keybase to send encrypted messages. My main use case for this is sending credentials and things securely in situations where there's not a shared vault (e.g. 1Password, LastPass, Hashicorp's Vault) that I can just plop whatever into.
I had it all set up and ready to go on my last Macbook, FingerSkillet, but now I have a new Macbook so I need to do it again.
To go through this process you'll need to download:
- GPG Tools for macOS
- The Keybase CLI
You'll also need a Keybase account - if you do not have one of these, bug a friend to send you an invite and sign up!
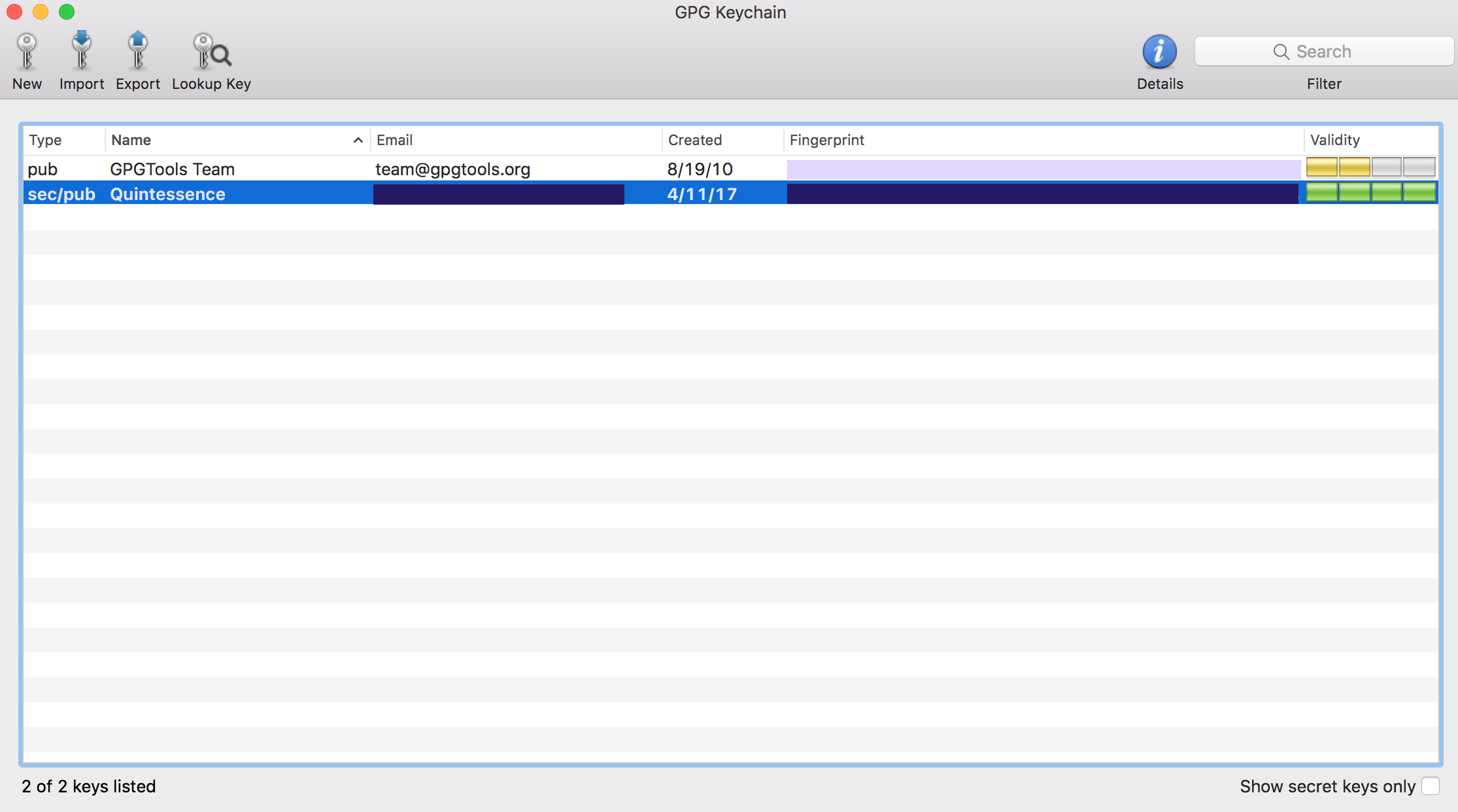
When you run the installer for GPG Tools you'll be prompted to create a new key with a strong passcode. Personally, I used 1Password to generate a nice long passcode and stored it in a secure note. I'd recommend doing something similar with your credential manager of choice. Once that's done it'd look a little like this:
Now for the Keybase setup. The installation is painless but then you get to actually logging in, which will look a bit like this:

Since I already have an account, I decided to see what the app would do if I tried to just log in with my credentials. Alas, it did not go well.
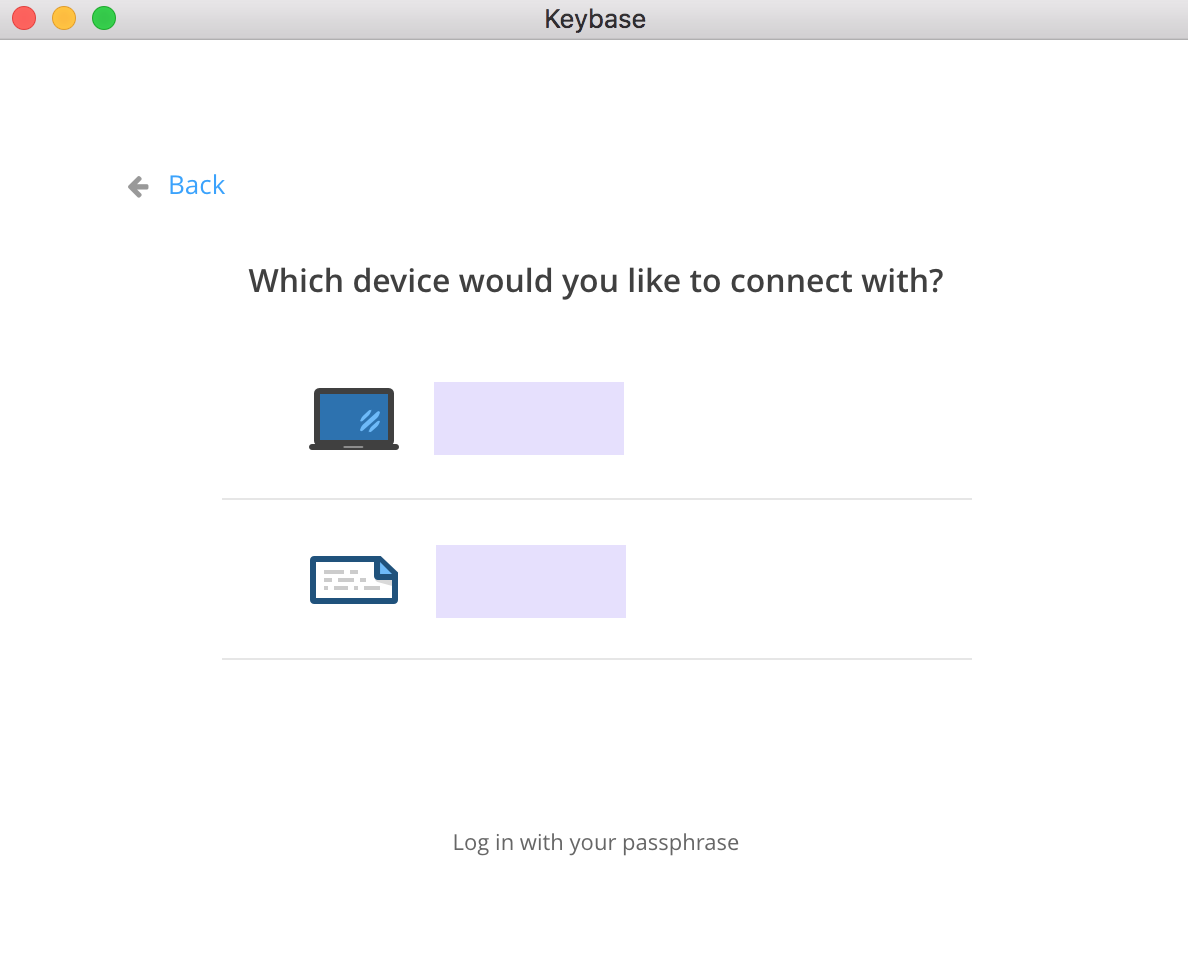
Since one of those methods is the laptop I'm migrating from I opted to just login with my passphrase:
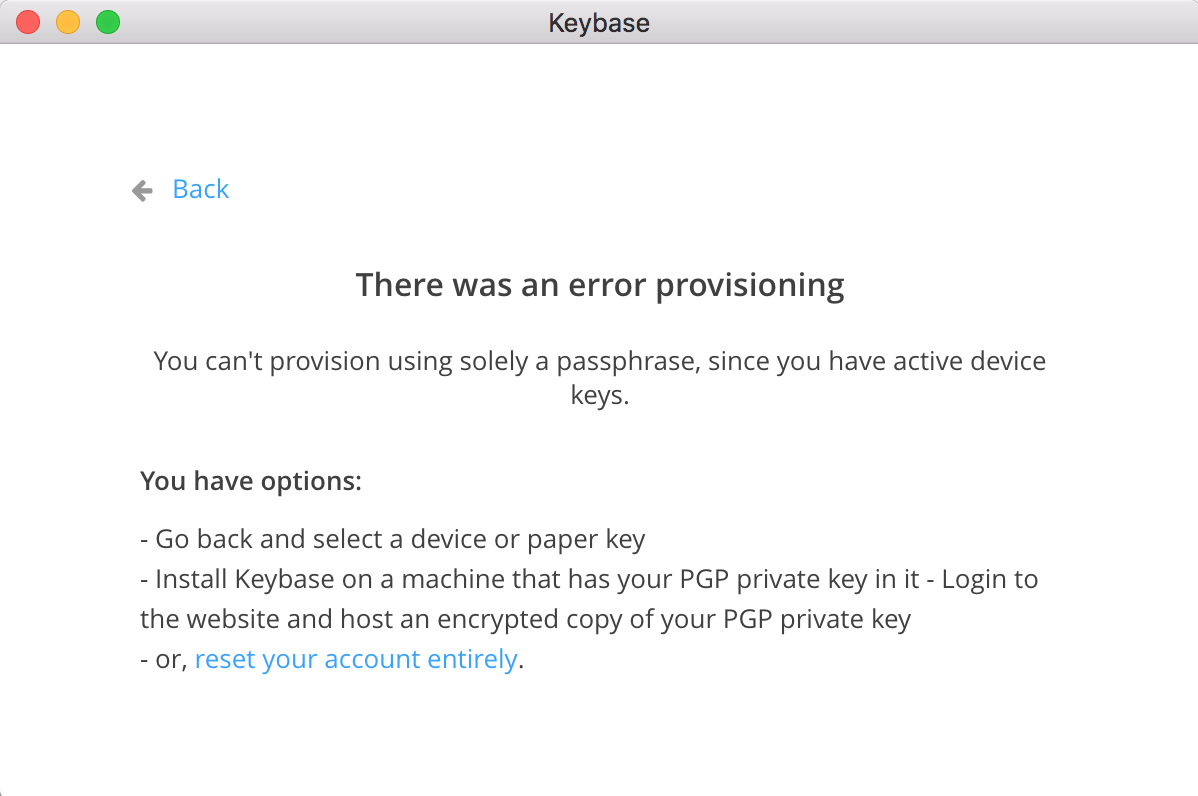
Oh snap!
Thank goodness for that paper key (good thing you set that up, ***right?***)
Rinse repeat the above, making sure to set up with that paper key, and you're in!
Now that I'm logged into Keybase, can I encrypt a message?
+22:30:20:324:0 quintessence@FingerSkilletII ~
→ keybase
-bash: keybase: command not found
ruh-roh. Well it looks like at least one other person had trouble installing the keybase CLI with the macOS app installer and that the CLI is supposed to be in /usr/local/bin. Let's see:
+22:32:05:325:127 quintessence@FingerSkilletII ~
→ ls /usr/local/bin/keybase
/usr/local/bin/keybase
+22:33:32:326:0 quintessence@FingerSkilletII ~
→ echo $PATH
/Users/quintessence/perl5/perlbrew/bin:/Users/quintessence/perl5/perlbrew/perls/perl-5.16.0/bin:/Users/quintessence/bin:/usr/local/opt/coreutils/libexec/gnubin:/usr/local/Cellar/gnu-indent/2.2.10/bin:/usr/local/sbin:/usr/local/bin:/usr/bin:/bin:/usr/sbin:/sbin:/usr/local/MacGPG2/bin
So it exists where it's supposed to and /usr/local/bin is in my path. Permissions issue?
+22:33:53:330:0 quintessence@FingerSkilletII ~
→ ls -lh /usr/local/bin/key*
lrwxr-xr-x 1 quintessence admin 60 Apr 22 22:32 /usr/local/bin/keybase -> /Applications/Keybase.app/Contents/SharedSupport/bin/keybase
Nope. But yet now:
+22:33:57:331:0 quintessence@FingerSkilletII ~
→ keybase
NAME:
keybase - Keybase command line client.
...
All right, moving along then.
I can still see my PGP key on Keybase:
+22:50:27:337:0 quintessence@FingerSkilletII ~
→ keybase pgp list
Keybase Key ID: <is here correctly>
PGP Fingerprint: <is also here correctly>
PGP Identities:
Quintessence <my@email.com>
And I can still (de|en)crypt messages, which is the whole point:
+22:53:02:340:0 quintessence@FingerSkilletII ~
→ keybase encrypt jhunt -m 'FingerSkillet II is here!'
BEGIN KEYBASE SALTPACK ENCRYPTED MESSAGE. <snip for length>. END KEYBASE SALTPACK ENCRYPTED MESSAGE.
+23:06:21:354:1 quintessence@FingerSkilletII ~
→ keybase decrypt -m "BEGIN KEYBASE SALTPACK ENCRYPTED MESSAGE.
<snip for length> END KEYBASE SALTPACK ENCRYPTED MESSAGE."
Message authored by jhunt
¯\_(ツ)_/¯
But only via saltpack.
What that means is, right now, I cannot decrypt a PGP message since the key that it uses is only on the old Mac and not the new one. Options are to either get the key from the old Mac to the new one or to simply revoke the key and generate a new one. I'm going with the latter:
+23:10:32:356:2 quintessence@FingerSkilletII ~
→ gpg --gen-key
gpg (GnuPG/MacGPG2) 2.0.30; Copyright (C) 2015 Free Software Foundation, Inc.
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law.
Please select what kind of key you want:
(1) RSA and RSA (default)
(2) DSA and Elgamal
(3) DSA (sign only)
(4) RSA (sign only)
Your selection? 1
RSA keys may be between 1024 and 4096 bits long.
What keysize do you want? (2048) 4096
Requested keysize is 4096 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 0
Key does not expire at all
Is this correct? (y/N) y
GnuPG needs to construct a user ID to identify your key.
Real name: Quintessence
Email address: my@email.com
Comment:
You selected this USER-ID:
"Quintessence <my@email.com>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? O
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
gpg: key SOMEIDENTIFIER marked as ultimately trusted
public and secret key created and signed.
gpg: checking the trustdb
gpg: 3 marginal(s) needed, 1 complete(s) needed, PGP trust model
gpg: depth: 0 valid: 2 signed: 0 trust: 0-, 0q, 0n, 0m, 0f, 2u
gpg: next trustdb check due at 2021-04-12
pub 4096R/SOMEIDENTIFIER 2017-04-25
Key fingerprint = <snip>
uid [ultimate] Quintessence <my@email.com>
sub 4096R/OTHERIDENT 2017-04-25
+23:16:07:357:0 quintessence@FingerSkilletII ~
→ keybase pgp list
Keybase Key ID: 0101...
PGP Fingerprint: <snip>
PGP Identities:
Quintessence <my@email.com>
+23:19:28:361:0 quintessence@FingerSkilletII ~
→ keybase pgp drop 0101...
▶ INFO Revoking KIDs:
▶ INFO 0101...
+23:20:08:373:0 quintessence@FingerSkilletII ~
→ keybase pgp select SOMEIDENTIFIER
# Algo Key Id Created UserId
= ==== ====== ======= ======
1 4096R <snip> Quintessence <my@email.com>
Choose a key: 1
▶ INFO Bundle unlocked: <snip>
▶ INFO Generated new PGP key:
▶ INFO user: Quintessence <my@email.com>
▶ INFO 4096-bit RSA key, ID <snip>, created 2017-04-24
▶ INFO Key <snip> imported
And now I can once more (en|de)crypt even PGP encrypted messages:
+23:45:42:376:0 quintessence@FingerSkilletII ~
→ keybase pgp decrypt -m "-----BEGIN PGP MESSAGE-----
> Comment: https://keybase.io/download
> Version: Keybase Go 1.0.18 (darwin)
>
> wcFMA6k8+13DFJU+ARAAsqdhnMe6+rMq2w1qMHGYVXHgBEOqJrYar/0fPsgi2FXp
> <snip>
> -----END PGP MESSAGE-----"
(╯°□°)╯︵ ┻━┻
It's worth noting that there was a brief period when presumably everything was updating that someone couldn't encrypt a message to me because they were only seeing that I had deleted a PGP key, not that I added a new one. This resolved in a few minutes.
▶ WARNING Some proofs were revoked:
✖ <Deleted proof: <snip> >
Some proofs are failing. [A]ccept these changes or [C]ancel?: A
Publish these changes publicly to keybase.io? [Y/n]